Just a quick drop of notes on how to configure this if anyone else needs it.
You probably searched the net and found tons of howtos on policy-based VPNs. However, I needed to do a route-based VPN my Azure resources with multi-devices and you can have only a single VPN-policy on a Gateway. Infos on IPSEC settings where taken from the Azure documentation - please make sure you read the fields marked important.
*Disclaimer: I just set this up and it works for me. I am not sure about the support from VMware or MS on this.
Overview
The picture shows the basic setup for this example:
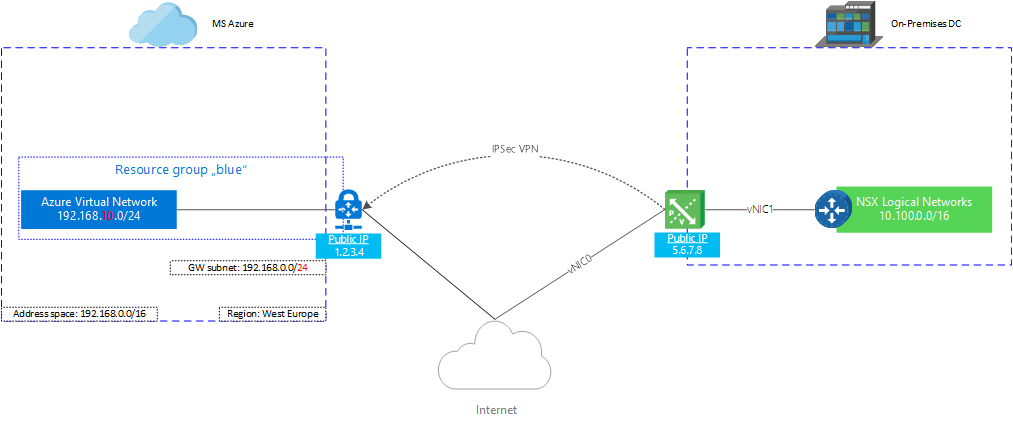
Azure
Network settings
**Address Space:** 192.168.0.0/16
**Resource Group:** blue
**Location:** West Europe
**Subnet:** 192.168.10.0/24
**Gateway Subnet:** 192.168.0.0/**24**
**Virtual Network Gateway Name:** AzureGW
**Public IP:** 1.2.3.4
**VPN Type:** Route-based
**Connection Type:** Site-to-site (IPsec)
**Gateway Type:** VPN
**Local Network Gateway Name:** On-PremisesDC
High-Level steps
- Create local network(s)
- Create VPN-Gateway with all dependencies
- Create local gateway
- Create VPN connection
Azure has a good documentation on the implementation steps make sure you follow it and adapt it to your environment.
NSX
Deploy an NSX Edge Gateway with a public IP on an uplink interface (in case of the example 5.6.7.8 on vNic0).
Edge VPN Settings
Create a new IPsec connection and fill out the values as required.
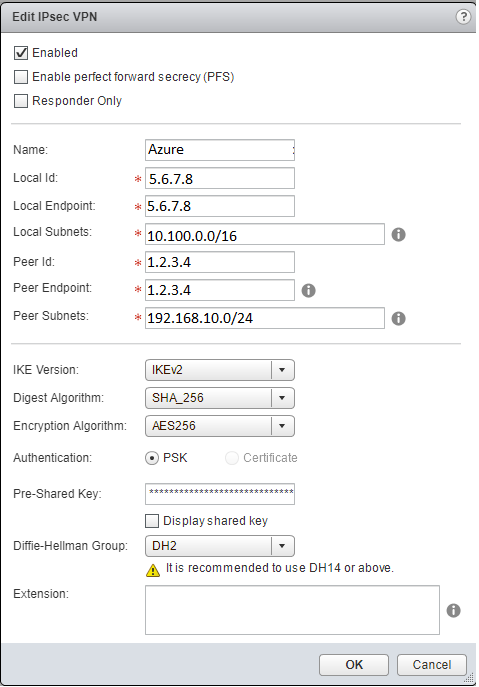
Start the IPSEC connection on the NSX Edge, it should take a minute or two until the connection is up and running.
You can check the connection details on the IPSec tab of the NSX edge or via the NSX Manager CLI
show edge <edge-id> service ipsec site
Comments